Summary
The initial OTSec Group launch and the subsequent communication on it have further emphasised the need for such a group in Ireland. A problem shared is a problem solved is a theme that echoed from the presenters and the participants at this initial event. Over the next few months more structure will be developed around the OTSec group, a committee will be formed, a set of themes for further webinars, workshops and events will be finalised and if you and/or your company would like to participate, you can complete our survey and join our mailing list.
What will you find in this Blog Post?
1. OTSec Working Group Overview
2. 1st Talk: Siemens and The Secrets of Stuxnet
3. 2nd Talk: OTSec Challenges in The Pharmaceutical Sector
4. Q&A Discussion
5. OTSec Group Launch Video
6. Participants Survey Results

Overview
In recent months and weeks it has become clear that many in society have only just become aware of the danger of Cyber threats due to the very public nature of the HSE and the Colonial pipeline attacks. While these events are evidence of the larger picture and the eventual realization that “something must be done” it is a problem that industry has been dealing with for over two decades. However, the complexity, volume, regularity and scale of attack is on the increase, facilitated by advances in technology. These attacks are used to either leverage money or damage infrastructure and ultimately impact upon economic output.
It is fair to say that while the reasons for attacks in Operations Technology (OT) on Industrial Control Systems (ICS) and utilities such as water, electricity, rail, air services and other infrastructure are the same as attacks on Information Technology (IT), the potential for physical damage and risk of human causalities and death is increased. Priorities are also different with OT process uptime and availability key to the maintenance of utility services and manufacturing process output.
These events and developments were the catalyst to development of this Cyber Ireland Special Interest Group (SIG) to focus on OT Security (OTSec). Rather than considering solutions, the initial meeting on the 16th June focused on the root of the problem, as it pertains to the OT of ICS.
115 people registered for this initial launch which was hosted by Dr Diarmuid Ó Briain form the Faculty of Engineering at the institute of Technology in Carlow. There were two main speakers:
Siemens and The Secrets of Stuxnet

Wayne Bursey the Industrial Cyber Security Lead for Siemens Ireland and Scotland brought the group through the journey taken by Siemens, once they had digested the enormity of the Stuxnet attack on their Step 7 PLC at an Iranian Centrifuge in Iran. It caused Siemens to consider Cyber risk not just in the context of their products but across their organisation in a new way.
The key takeaways from Wayne’s presentation were:
• Lessons Learned 1: Have a process for vulnerability handling!
• Lessons Learned 2: Take a leading standard and apply it!
◦ Defense-in-Depth-Concept based on IEC-62443
• Lessons Learned 3: Build a Security Network
Siemens Certifications in Cybersecurity today include ACHILLES, IEC 62443 and ANSSI certification (CSPN) demonstrating their committent to Cybersecurity both within their organisation, in their products and in their ability to assist their customers at their time of need.
To see Wayne’s Slide Deck, Click Here
OTSec Challenges in The Pharmaceutical Sector

Eamonn O’Mara is the Site IT lead at Merck Sharp & Dohme (MSD) in Carlow, he is tasked with the defence of a next in class Pharmaceutical manufacturing plant that is part of a wider network of plants within MSD, but also within the wider key Pharmaceutical manufacturing sector of the Irish economy. Eamonn gave a fascinating insight into the thought process of a defender. He started with a thought provoking quote from Dr Bruce Schneier the Chief of Security Architecture at Inrupt, Inc.
“If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.”
He outlined that the IT priority is protecting data while the priority of OT teams is process and production and “one size does NOT fit all“. The IT approach of patching and updating may not be possible in extended life OT infrastructure and could be detrimental to production due to unintended consequences.
OT requires careful selection of the security technology as they are not like IT solutions. Ensure that selected solutions incorporate flexibility and can accommodate many partners.
The key takeaway from Eamonn’s presentation are the following Nine Principles:
1. Establish and support a Common OT Security Architecture Baseline
2. Maintain an awareness of major manufacturing and research programmes underway
3. Facilitate partnership to support major IT Risk Management Systems programmes
4. Monitor and participate in industry peer conversations and feedback
5. Be aware of technology research, vendor presentations and share success stories
6. Maintain multiple Cross-Divisional alignment as part of Annual Portfolio Planning
7. Review current issues, pain points, address questions with existing OT security controls
8. Execute periodic reviews of internal guidelines and industry standards
9. Act as a unified voice and share success stories
To see Eamonn’s Slide Deck, Click Here
OTSec Survey
The webinar also asked the participants to partake in a short survey to determine attitudes and future direction for the OTSec group.
The attendees came from various types of organisations: cyber-consumer, internal OTSec team, vendors, integrators, academia and government. There was a mix of the level of expertise across beginners, intermediate or advanced level.
Q4: What is your level of expertise regarding Operational Technology (OT) Cybersecurity?
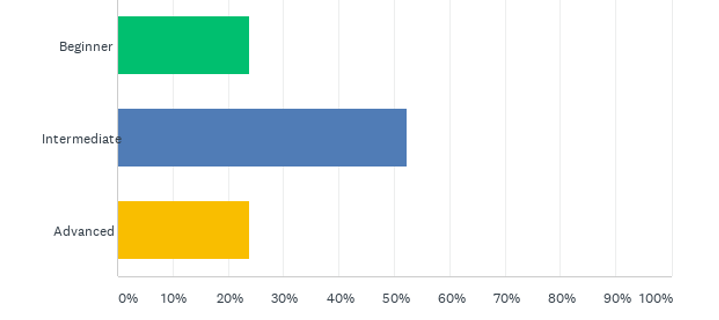
Surprisingly, 53% of participants’ organisation did not have a cybersecurity posture. This is worrying as the attendees are obviously aware of the threat and without a cybersecurity posture their organisations are leaving themselves vulnerable. While 40% of participants were unaware if their IT and OT were separated in their organisation, of those that answered, it appears that the majority of organisations represented choose to separate IT and OT and with a firewall rather that a firebreak.
Participants were asked to consider the most significant challenges around OTSec for companies:
- Organisations not having a clear OT strategy
- Managing the differences between IT / OT and integration
- Skills and Experience needed to manage OT through continuous change
- Software vulnerability management with OT assets that may remain in service for 10+ years
- A confusion of messaging from vendors and third party solutions that do not adapt, scale or are immature
- The balancing act of managing risk and regulatory compliance.
The list of challenges is large and one of the initial drivers for the OTSec group is to provide a forum to discuss these problems and success stories between members.
The primary reasons why participants are interested in joining an OTSec group are:
- Information and knowledge sharing
- Openly discuss the challenges of OT Security
- A forum to connect consumers, integrators and vendors
There was a long list of goals and activities submitted and over the next few months a committee will form to drive these goals through the organisation of events and workshops. If you and/or your company would like to participate in the OTSec Group then please complete the survey and join our mailing list.

